While doing some research on the use of golang in malware, I came across this golang sample here: https://www.virustotal.com/gui/file/020f6b3e045fa6b968226a8f2b2800dc55c65e842607d04d68b47ef4d18b0eee/detection
At the time of writing this, it has 3/72 detections.
It's named winnta.exe
MD5 7e17c9e4ebe61e43966e9f65e334727e
SHA-1 2172901d2a13304dd53a83e518fd5be84ed9ec08
SHA-256 020f6b3e045fa6b968226a8f2b2800dc55c65e842607d04d68b47ef4d18b0eee
Here are the results for yara scan: https://yaraify.abuse.ch/sample/020f6b3e045fa6b968226a8f2b2800dc55c65e842607d04d68b47ef4d18b0eee/
It connects to 195.149.87[.]87:443 (https://www.virustotal.com/gui/ip-address/195.149.87.87/relations )
The data above doesn't really tell us much about the sample.
Running strings on the sample is kinda interesting, it shows the following:
-ldflags="-s -w -extldflags '-static' -X main.name=WindowsNTApp -X main.addr=195.149.87.87:443 -X main.service=WindowsNTApp"
Also there are a bunch of references to go files and code in this directory: "/home/builder18g/goroot/" for example:
/home/builder18g/goroot/src/c/gsh/main/main.go
/home/builder18g/goroot/src/c/gsh/main/windows.go
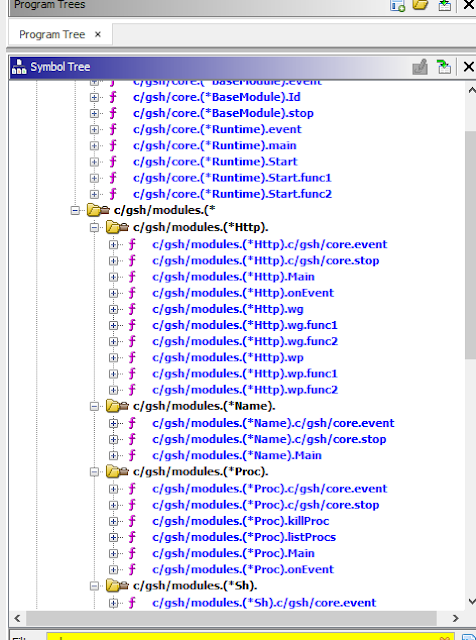
Looking for 'main.' shows the following:
runtime.main.func1
runtime.main.func2
main.main
main.(*winService).Stop
main.(*winService).Execute
main.(*winService).Start
main.(*winService).Execute.func1
main.startInteractive
main.Start
At this point, assumption is this is some kinda backdoor.
Researching the C2 IP, I found this:
https://raw.githubusercontent.com/stamparm/maltrail/master/trails/static/malware/apt_unc961.txt
https://otx.alienvault.com/pulse/6244606893ddbc9a6a5bbdeb
https://www.mandiant.com/resources/blog/mobileiron-log4shell-exploitation
Here's what Mandiant has to say about this:
"UNC961 deployed two previously unobserved backdoors: HOLEDOOR and DARKDOOR. HOLEDOOR is written in C, whereas DARKDOOR is written in Go."
"DARKDOOR is a backdoor written in Go that is highly modular in design. It supports communication over TLS and HTTP. It has capabilities to execute arbitrary code and list running processes."
I continued to do more research to see what else I can find out about this sample doing any reverse engineering.
Searching for winnta.exe results in a paper from SentinelOne (https://www.sentinelone.com/wp-content/uploads/2021/05/Watchtower_2021_May_White.pdf)
They mention the backdoor under section "Mercenary APT Groups Targeting the Financial Services Industry"
Here's what they had to say about it:
File: winntaWindows EXE written in golang that calls out to
45.76.236[.]136:443
Backdoor functionality
Potential name “gsh”
File: main
Golang compiled EXE of same “gsh” family as mentioned
for winnta
Calls out to 198.199.104[.]97:443 and has backdoor
capabilities
Under potential attribution section, they refer to an RSA report regarding Carbanak."Carbanak has been reported using a custom golang backdoor named GOTROJ. This backdoor
has code overlap and functionality similar to the “geodezine” backdoor discovered in the attacker’s toolkit. "
The RSA paper "The Shadows of Ghosts" can be found here: https://www.netwitness.com/wp-content/uploads/2021/12/the-shadows-of-ghosts-carbanak-report.pdf
Here's a snippet about GOTROJ from the paper:
"On D+30, the attackers installed a Windows Trojan, written in Go, as a Windows
Service on one of the two primary Active Directory Domain Controllers. They
would move to utilizing the GOTROJ as their primary method of ingress for the
duration of the engagement. The GOTROJ Trojan communicated with C2 IP
address 107.181.246.146 over TCP/443 for its remote access channel."
I continued doing more research. I searched for "WindowsNTApp" service, which came up with a crowdstrike report on ProphetSpider. The report is here: https://www.crowdstrike.com/blog/prophet-spider-exploits-oracle-weblogic-to-facilitate-ransomware-activity/
They also refer to the malware as GOTROJ. This is what they say:
"The adversary commonly creates Windows services, e.g. WindowsNTApp for GOTROJ, to establish persistence for downloaded malware."